From regulation to resilience
Turn compliance into strength. Trustlinks helps you manage risks, protect
assets, and build trust across your organisation and supply chain.
TRUSTLINKS PRODUCT TOURTrustlinks system overview
Take a guided tour of Trustlinks and learn how the platform supports organisations in meeting regulatory requirements.
The system enables secure reporting, structured documentation, and efficient handling of incidents, while ensuring
management accountability and risk-based security measures. From initial assessment to continuous compliance,
Trustlinks provides a clear and reliable framework for building resilience and trust.
Frameworks
Easily align with leading frameworks. Our framework module streamlines compliance mapping, so you can demonstrate adherence, identify overlaps, and focus resources where they matter most.
Chapters
Break down complex frameworks into clear, manageable chapters. Navigate requirements step by step, making it easier for teams to understand obligations and structure compliance efforts efficiently.
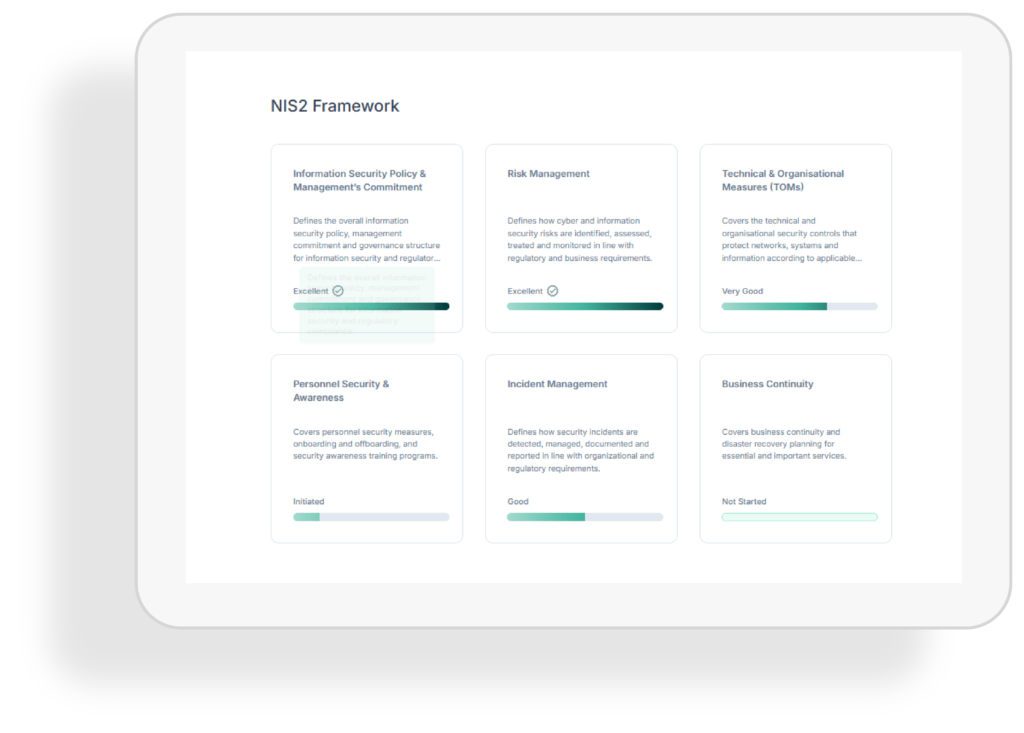
Compliance status
See exactly where you stand within each framework. Visual indicators highlight completed, pending, or missing measures, helping you stay aligned and prioritise actions where they matter most.
Suggestions per chapter
Receive practical, AI-driven suggestions for each framework chapter. Get actionable guidance tailored to your context, simplifying compliance work and ensuring your organisation addresses requirements effectively.
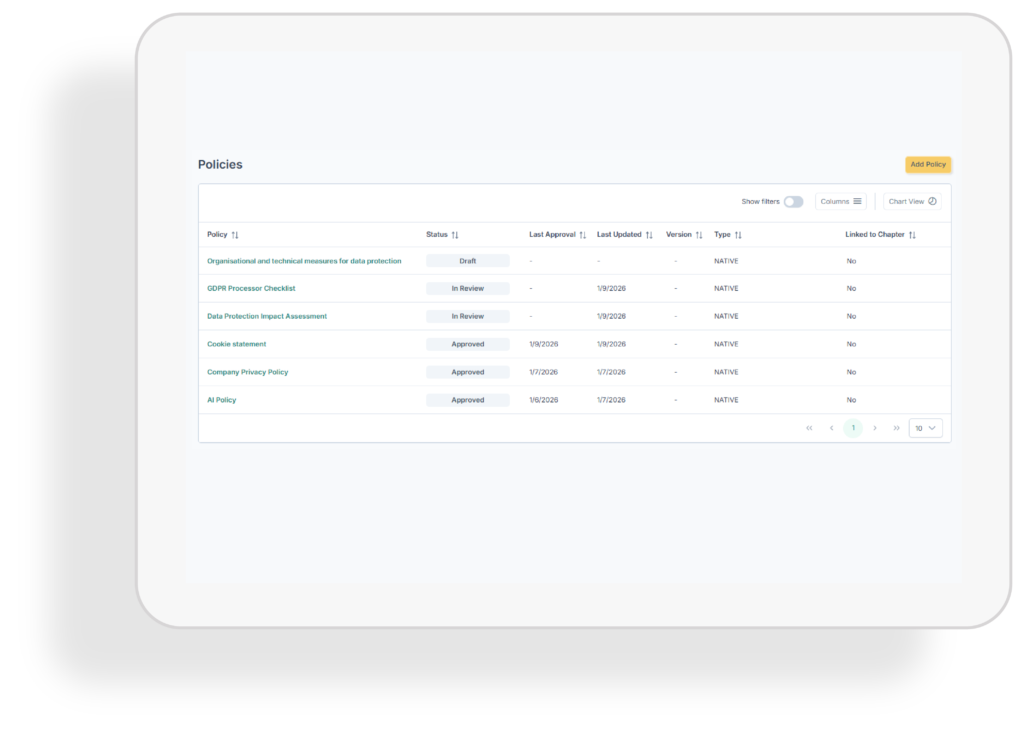
Policies
Centralise and manage policies across your organisation. Ensure your teams follow consistent, up-to-date guidelines with built-in version control and easy access for audits and compliance checks.
Policy library
Centralise all your organisation’s policies in one secure library. Easily access, organise, and maintain up-to-date documents for compliance, audits, and everyday operations.
Templates
Accelerate policy creation with ready-to-use templates. Ensure best practices are followed while saving time and reducing the complexity of drafting documents from scratch.
Import document
Seamlessly import existing policies into the platform. Keep everything in one place for easier management, consistency, and compliance visibility.
Create and edit docs
Draft and edit policies directly within the platform. Collaborate efficiently, track changes, and maintain full version control across your organisation.
Link to external docs
Connect your SharePoint or external repositories. Ensure policies remain accessible and synchronised, while preserving a single source of truth for compliance.
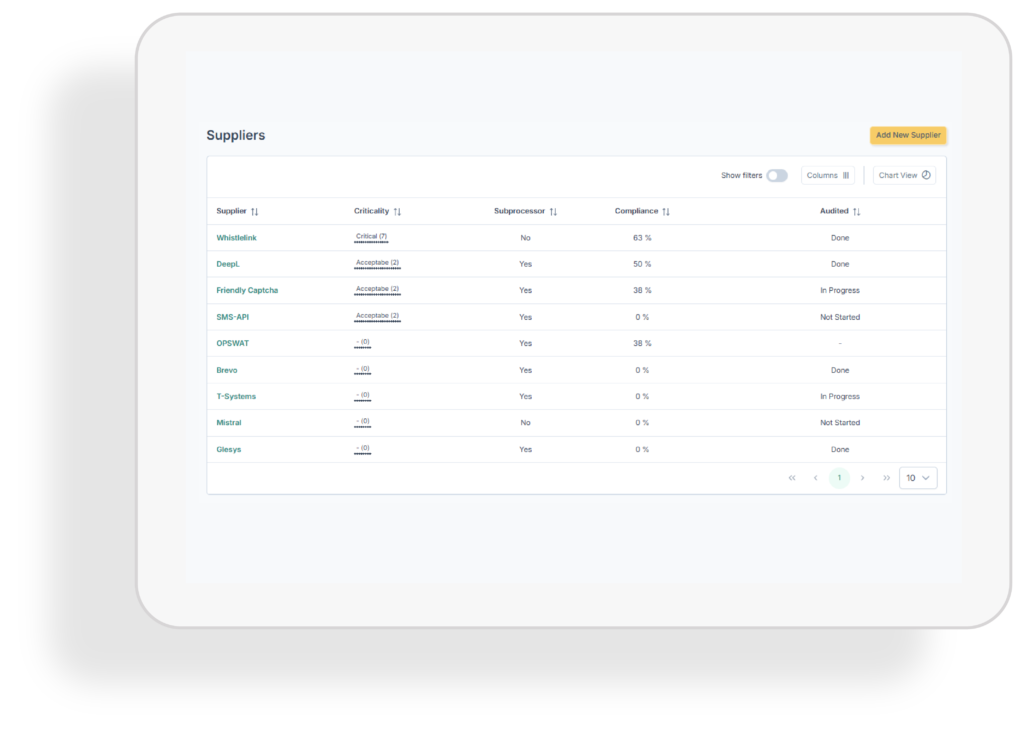
Suppliers
Strengthen supply chain security with streamlined supplier assessments and monitoring. Gain visibility into third-party risks, and maintain trust by ensuring your partners meet regulatory and contractual cybersecurity requirements.
Supplier directory
Keep all supplier information organised in one directory. Gain quick access to contacts, contracts, and compliance details for efficient supplier management.
Supplier assessment
Evaluate supplier security posture with structured assessments. Identify gaps, ensure compliance with requirements, and strengthen overall supply chain resilience.
Risk assessments
Perform supplier-specific risk assessments to uncover vulnerabilities. Monitor exposure, track mitigation, and ensure third parties meet your cybersecurity standards.
Supplier chain map
Visualise your supply chain with an interactive map. Understand dependencies, identify weak links, and build greater transparency into third-party relationships.
Risks
Identify, assess, and manage risks through an integrated risk register. The module simplifies threat prioritization and mitigation planning, empowering you to make informed decisions and strengthen resilience against evolving cyber threats.
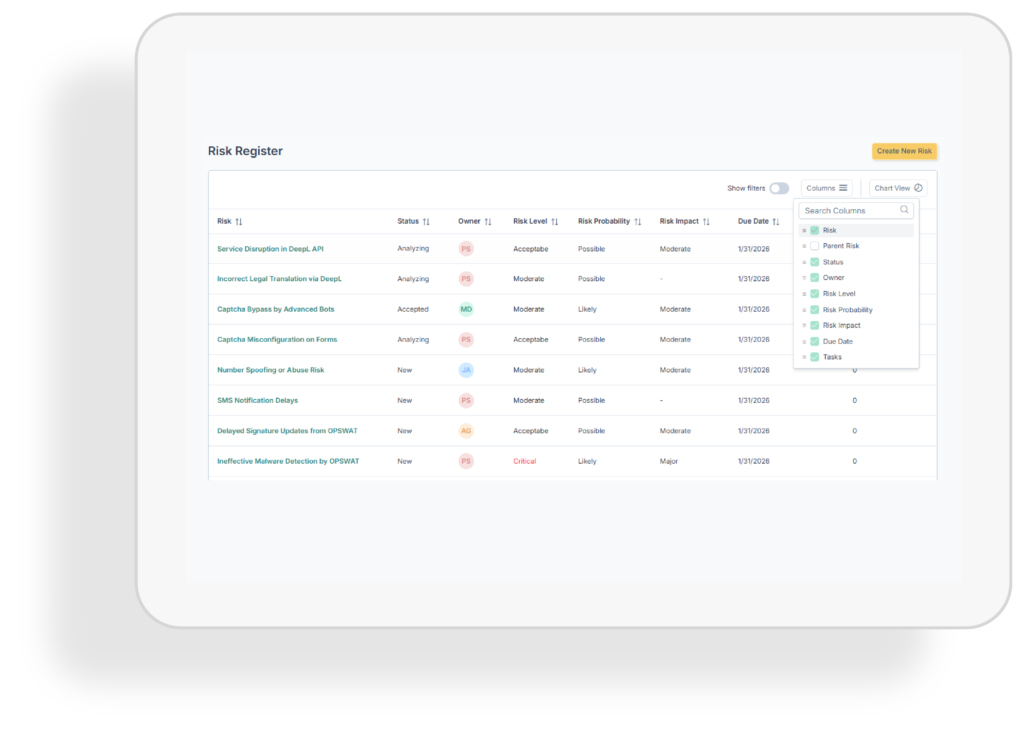
Risk register
Central risk register to document threats, vulnerabilities, and controls. Keep all risk information structured, traceable, and audit-ready in one accessible place.
Risk model
Standardised risk model to evaluate potential threats consistently. Ensure reliable comparisons across risks and support smarter, evidence-based decision-making.
Risk matrix
Visualise risks in a clear matrix. Quickly identify high-impact, high-likelihood threats and prioritize mitigation efforts with confidence.
Risk assessment
Conduct structured risk assessments with guided workflows. Identify weaknesses, evaluate potential impacts, and build a strong foundation for proactive risk management.
Mitigation plans
Define and track clear mitigation actions for each risk. Ensure accountability, monitor progress, and reduce exposure with structured, measurable plans.
Heatmaps
Transform complex risk data into intuitive heatmaps. Gain instant insights into organisational risk posture and communicate priorities effectively to management and stakeholders.
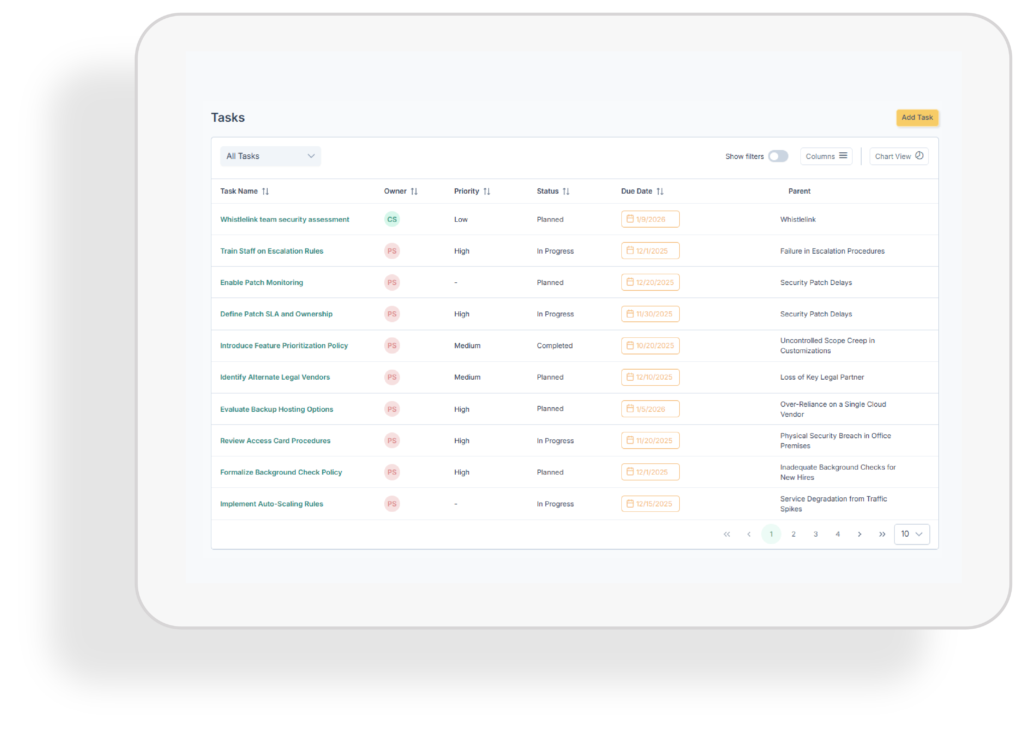
Tasks
Assign, track, and monitor compliance and security tasks in one place. From incident response to policy updates, the task manager ensures accountability, deadlines, and progress visibility across your organisation.
Tasks register
Keep every compliance and security task in one structured register. Ensure nothing slips through the cracks with a clear, centralised view of all activities.
Tasks overview
Access a calendar-based view of your task register to track ongoing and completed activities. Easily spot upcoming deadlines, prevent delays, and maintain clear visibility across compliance efforts.
Task owners
Assign clear ownership to each task. Strengthen accountability by ensuring responsibilities are transparent and progress is tracked effectively.
Deadlines
Set and manage deadlines to stay on schedule. Ensure timely completion of critical compliance and security actions with clear due dates.
Notifications
Receive smart notifications and reminders. Stay informed of upcoming deadlines, overdue tasks, and updates without relying on manual follow-ups.
Reoccurance tasks
Automate recurring compliance and security tasks. Save time, maintain consistency, and ensure critical actions are never overlooked.
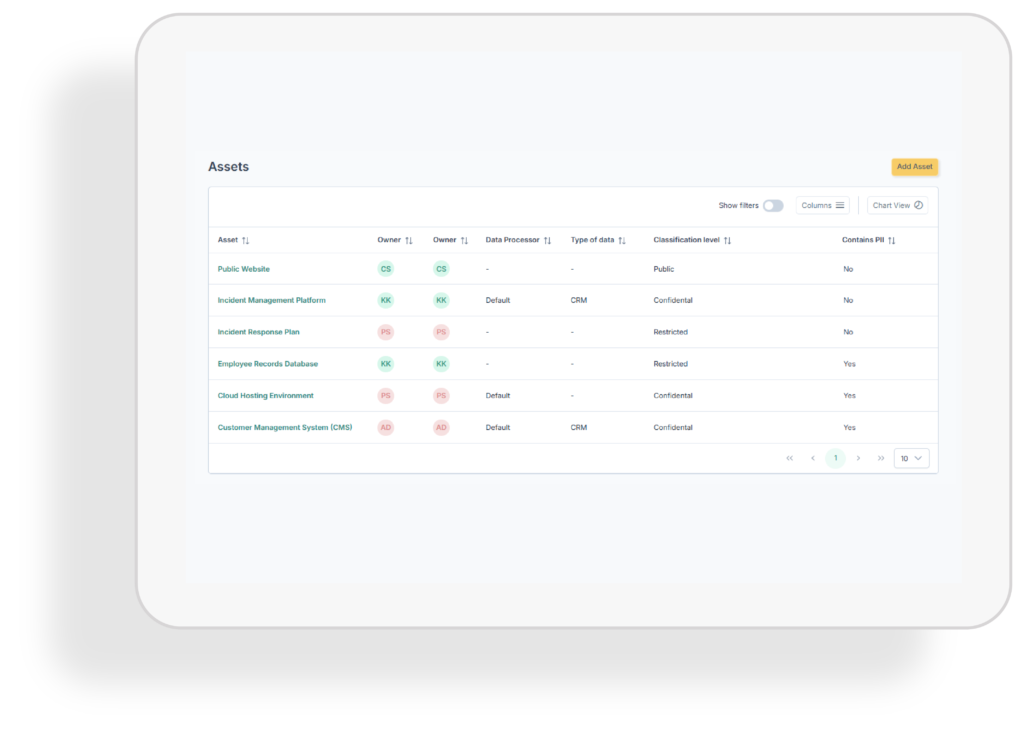
Assets
Maintain a structured inventory of your digital and physical assets. With clear visibility of critical systems, applications, and data, you can better protect what matters, reduce risks, and support compliance with regulations.
Asset inventory
Keep track of all your critical assets in one structured inventory. Gain visibility into systems, applications, and data, ensuring nothing vital is overlooked in your cybersecurity strategy.
Classification & ownership
Classify assets by criticality and assign clear ownership. This ensures accountability, helps prioritise protection measures, and strengthens compliance with regulations requiring structured asset management.

Incidents
Stay prepared with structured incident management. Report, track, and resolve security events within regulatory timelines, while maintaining a clear audit trail. The module helps your team act quickly, stay compliant, and minimise impact.
Incident reporting
Capture and document incidents in a structured way. Ensure accurate, timely reporting that meets compliance requirements while providing a clear audit trail.
Triage & classification
Classify incidents by severity and type to prioritise response efforts. Streamline triage processes and ensure critical events are handled first.
Regulator reporting
Meet strict reporting requirements with following guidelines. Submit accurate updates within mandated timelines and reduce administrative burden.
Timeline
The timeline functionality informs clients of mandatory incident reporting deadlines, ensuring awareness of initial, follow-up, and final notification requirements, aligned with directive obligations and national variations.
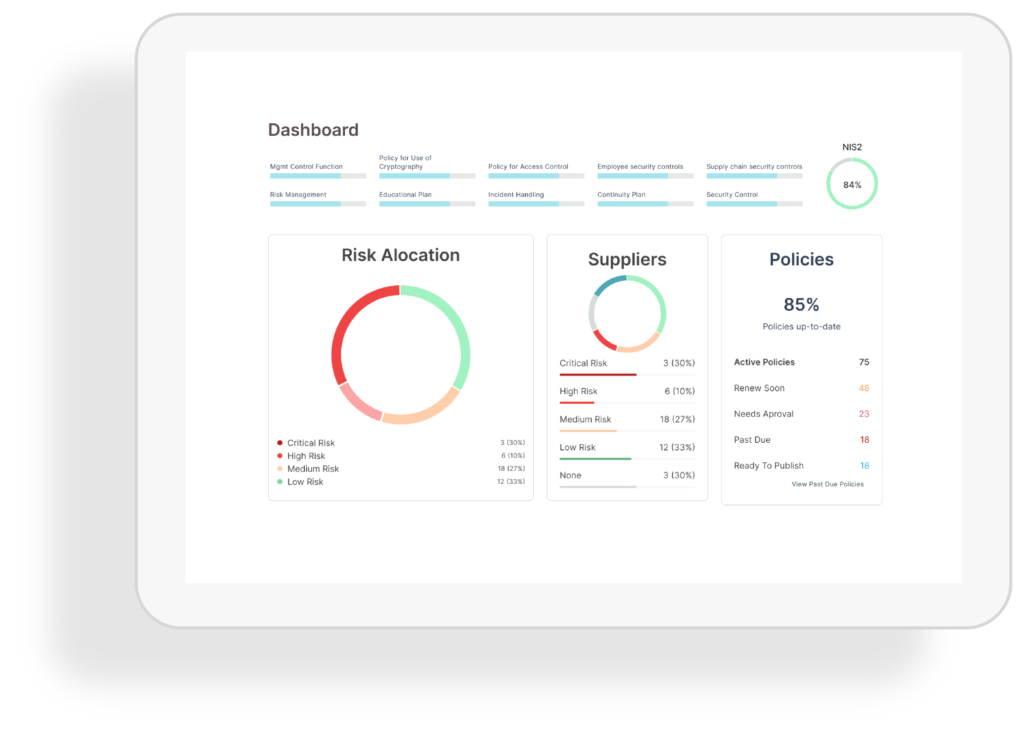
Dashboard
Complete overview of your compliance efforts in one place. The dashboard provides real-time insights and visual summaries, helping your team track progress, address gaps, and stay on top of critical requirements with ease.
Overview & KPI:s
Key performance indicators and security metrics in one glance. The overview gives real-time insights into progress, highlighting strengths and gaps to keep your compliance journey on course.
Compliance status
The compliance view shows how your organisation aligns with your chosen frameworks. Simplifies complex requirements into clear statuses, helping you identify areas that need attention.
Management report
Concise, board-ready reports with just a click. Management reports transform compliance data into strategic insights, enabling leadership to make informed decisions and demonstrate accountability.

AI
Leverage AI-powered insights to accelerate compliance, automate reporting, and detect anomalies. Our AI assistant helps you identify gaps, generate documentation, and support decision-making, reducing manual work and strengthening cyber resilience.
Risk predictions
Leverage AI to anticipate emerging risks before they escalate. Gain proactive insights into potential threats and adjust your security strategy with data-driven confidence.
Policy creation
Generate tailored policies with AI assistance. Save time, ensure alignment with frameworks, and reduce errors while maintaining compliance with evolving regulations.
Risk mitigations
Get AI-powered recommendations for effective risk mitigation. Identify the most impactful actions, prioritise resources, and strengthen resilience with smart, automated guidance.
Trust Center
Build transparency and confidence with a dedicated trust center. Share certifications, policies, and compliance status with, customers, prospects, partners and other stakeholders, strengthening relationships and showcasing your commitment to cybersecurity and regulatory excellence.
Public page
Showcase your organisation’s compliance, certifications, and security commitments on a dedicated public page. Build transparency and trust with stakeholders by sharing verified information in a clear, accessible format.
Customisable
Easily tailor your trust center to reflect your brand and priorities. Highlight the information most relevant to customers, partners, or auditors, ensuring your transparency hub communicates the right message to the right audience.

GDPR & Security
Securing your data is our highest priority and privacy is at the core of what we are doing. Whistleblowing Solutions AB, the company behind Trustlinks is certified with ISO 27001, Information security. Our focus is always on security and GDPR.
Hosting
The quality of hosting is crucial. The same goes for GDPR compliant hosting. Trustlinks is hosted entirely in Sweden and no data is processed or stored outside of EU.
Access control
Make sure data is kept confidential through the access control and user roles.
Single Sign-on
Our Single Sign-On (SSO) solution improves security and convenience by allowing seamless login with Microsoft accounts. This simplifies user management while ensuring strong access control and data protection.
2FA
The 2FA functionality ensures a secure login. The organisation can chose to make this mandatory for everyone on the team.
Encryption
All sensitive data is encrypted in rest using AES256 algorithm. The encryption keys used are handled by a Key Management System and by that stored safely.
Partners
Many partners have chosen Trustlinks as their preferred compliance platform and offer the system as part of a comprehensive solution. This includes law firms, audit firms, and compliance firms.
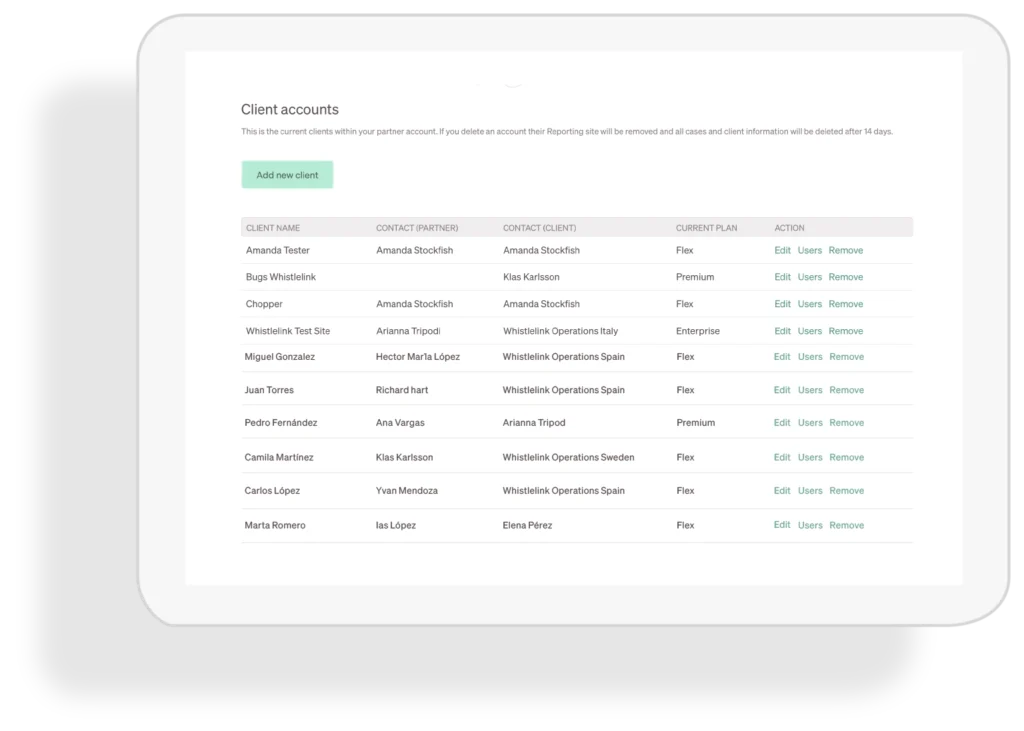
Set up and manage your own clients
Add new and manage existing clients in the partner module.
Partner branding
A partner has the option to add their logotype in the system.
LET'S GET IN TOUCH!Want us to tell you more?
Find out how Whistlelink can support your organisation. You simply choose when, and we’ll explain the why’s and how’s!


